Integrate CI-driven scans
This document outlines a generic process to integrate Invicti Platform with your CI/CD pipelines (for example, Jenkins, GitLab CI/CD, Azure Pipelines) to automate web application vulnerability scans. With this integration, you can automatically trigger security scans during your CI/CD workflows to identify and address issues before deployment.
Prerequisites
Ensure the following requirements are met before proceeding with the integration:
- Access to your CI/CD tool (Jenkins, GitLab CI/CD, Azure Pipelines, CircleCI, etc.)
- Docker command-line tool installed and running
- Invicti Platform account with API Security enabled
- Access to the Invicti Scan command-line tool Docker image. Refer to the access Invicti registries document for more information.
Step 1: Generate an API Token
You need an API token to authenticate the scan requests.
- In Invicti Platform, choose your Username > Profile from the left-side menu.
- In the Token field, copy the existing token. If you generate a new token, the previous one becomes invalidated.
- Store this token securely. It is used in your CI/CD script.
Step 2: Generate an automated scan script
Invicti Platform provides a tool-specific scan script generator. This script can be adapted for any CI/CD tool.
- Choose Integrations from the left-side menu.
- Open the Browse Integrations tab.
- Choose any supported integration (for example, Jenkins) to generate a base script and click Configure.
- Choose the Asset and Scan Profile you want to use.
- Set build failure conditions if needed.
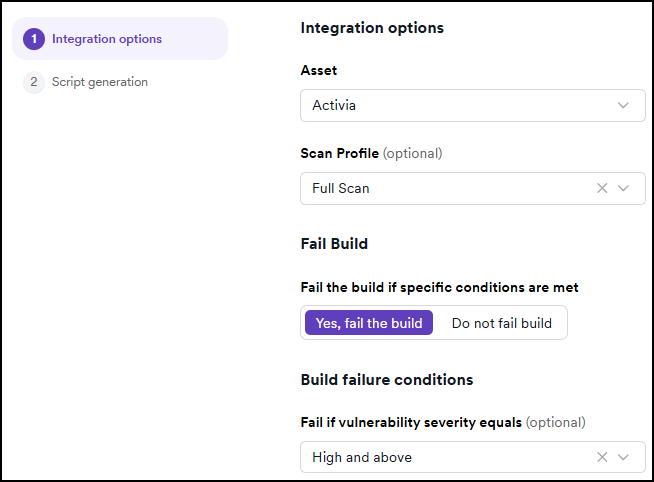
- Click Generate script.
Step 3: Copy and customize the script
- Copy the generated script.
- Replace the
INVICTI_API_TOKENplaceholder with your actual API token. - If needed, adjust environment variables or parameters to fit your CI/CD environment. For a list of all available variables, refer to the linked document.
Generic Docker Run commands for CI/CD scans
This provides a generic docker run command to execute Invicti DAST scans via the Invicti Scan command-line tool. This method can be used across all CI/CD platforms that support Docker.
Basic usage
Use the following command to trigger a scan directly via Docker:
docker pull platform.invicti.com/invicti-platform/invicti-scan-cli
docker run \
-e INVICTI_API_BASE_URL="https://platform.invicti.com" \
-e INVICTI_API_TOKEN="<your-api-token>" \
-e INVICTI_TARGET_ID="<your-target-id>" \
-e INVICTI_SCAN_AGENT="CloudAgent" \
-e INVICTI_REPORT_TEMPLATE="Comprehensive" \
platform.invicti.com/invicti-platform/invicti-scan-cli
This runs the scan using the configured target, agent, and report template. All scan data is stored and viewable in Invicti Platform.
With report volume mount
To retrieve reports locally after the scan completes, use a volume mount:
docker run \
-e INVICTI_API_BASE_URL="https://platform.invicti.com" \
-e INVICTI_API_TOKEN="<your-api-token>" \
-e INVICTI_TARGET_ID="<your-target-id>" \
-e INVICTI_SCAN_AGENT="CloudAgent" \
-e INVICTI_REPORT_TEMPLATE="Comprehensive" \
-v ./publicdata:/home/invicti/publicdata/ \
platform.invicti.com/invicti-platform/invicti-scan-cli
This mounts the local ./publicdata directory into the command-line tool container, allowing you to retrieve reports post-scan.
Step 4: Embed the script in your CI/CD pipeline
Each CI/CD tool has its own method for embedding shell scripts. Here's how to adapt:
- Jenkins: Add the script to the pipeline configuration.
- GitLab CI/CD: Place the script in a job step within your
.gitlab-ci.ymlfile. - Azure Pipelines: Add the script in a script step within your
azure-pipelines.ymlfile. - CircleCI: Create a file named
config.ymlinside the.circlecidirectory and paste the prepared script (Read more at the official CircleCI website)
Make sure the script runs at the appropriate phase (for example, post-build, pre-deploy).
Step 5: Run and monitor the pipeline
- Trigger a pipeline run.
- The CI/CD tool performs the following actions:
- Pull the Invicti Scan command-line tool Docker image
- Run the scan
- Generate a security report
- Monitor the console/log output.
- Download and review the report if required.
Additional tips
- Schedule regular scans using scheduled pipelines or cron jobs.
- Use environment-specific scan profiles (for example, staging vs. production).
- Integrate report output into your QA dashboards.
- Enforce policies to block builds if critical vulnerabilities are found.
Need help?
Invicti Support team is ready to provide you with technical help. Go to Help Center