Package: Invicti API Security Standalone or Bundle
NTA with Istio Mesh Service
This document explains how to install and configure the Invicti Network Traffic Analyzer (NTA) with Istio Service Mesh in your Kubernetes cluster to capture both HTTP and HTTPS traffic and reconstruct OpenAPI3 specification files.
Prerequisites
- A Kubernetes cluster
- Helm command-line tool installed (version 3+)
- kubectl configured for your cluster (for example, using Get-AksHciCredential)
- A Kubernetes namespace created for Invicti NTA
- Istio Service Mesh installed and running in your cluster
Minimum system requirements
- 1 GB RAM
- 2-core 64-bit CPU
- 2 GB available HDD
Overview
There are two ways to capture Kubernetes traffic with the Invicti NTA:
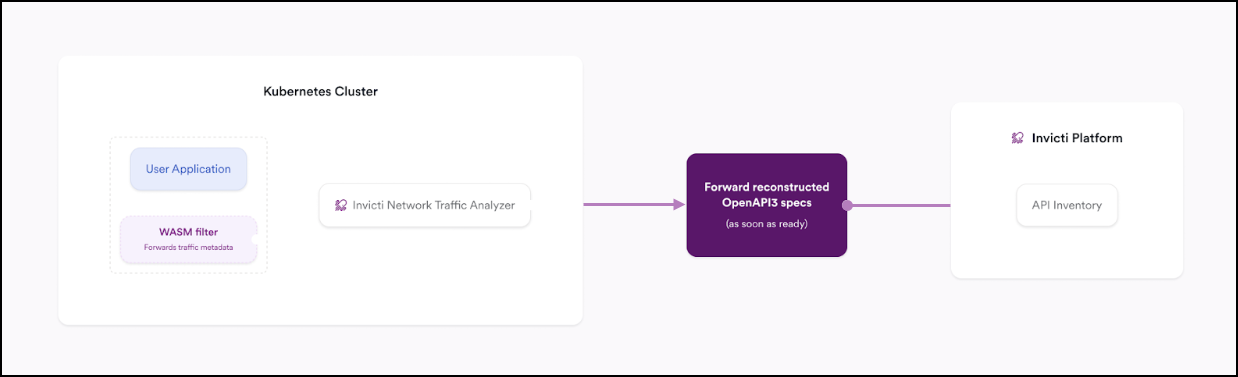
- Integrating with Istio Service Mesh (captures both HTTP & HTTPS traffic): This method is described in this document and leverages the Istio Envoy proxy with WASM filters to inspect encrypted (HTTPS) and unencrypted (HTTP) traffic. This document focuses on configuring Invicti NTA for this integration.
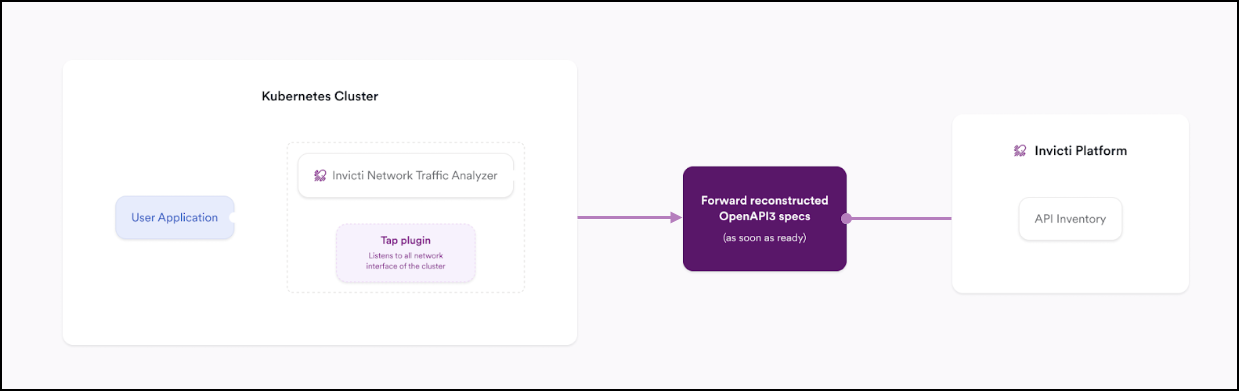
- Integrating with a Kubernetes namespace interface natively (captures HTTP traffic only): This method uses the Tap Plugin to monitor unencrypted traffic within a Kubernetes namespace. It does not support HTTPS traffic unless combined with Istio. Details for this setup are covered in the NTA with Tap Plugin documentation.
Installation steps
The Invicti NTA Helm chart includes:
- Reconstructor - Processes captured traffic and generates OpenAPI3 specification files.
- Istio Service Mesh Envoy - Captures both HTTP and HTTPS traffic by integrating with Istio's Envoy proxy. This is essential for environments using Istio to handle encrypted traffic (HTTPS) through the Envoy proxy and WebAssembly (WASM) filters.
Step 1: Retrieve the registration token
- Select Discovery > Configuration from the left-side menu.
- Further down, select API sources.
- Click Add source.
- Leave the Import type as External platform.
- Enter a name for the source configuration. This helps you identify it later in your list of API sources.
- Select Invicti Network Traffic Analyzer as the Source type.
- Click Generate token.
- Click the copy icon next to the newly generated registration token.
- Click Save at the bottom of the page. Do not skip this step.
Step 2: Authenticate with the Invicti Registry
- Launch the Helm command-line tool that was set up during the prerequisites.
- Then run the following command:
helm registry login registry.invicti.com
Username: your Invicti Platform email
Password: your valid Invicti Platform license key
Step 3: Label target namespace
Before deploying, label the namespace to enable Istio sidecar injection:
kubectl label namespace <your-namespace> istio-injection=enabled
Step 4: Prepare and deploy the Invicti Helm chart
In your Helm command-line tool or terminal, run the following command to install Invicti NTA into your Kubernetes cluster:
helm install invicti-api-discovery \
oci://registry.invicti.com/invicti-api-discovery \
--version 25.11 \ # Optional: omit to pull the latest version
-n default \
--set imageRegistryUsername=email-address \
--set imageRegistryPassword=password \
--set reconstructor.JWT_TOKEN="registration-token" \
--set trafficSource.envoyWasm.enabled=true \
--set trafficSource.envoyWasm.namespaces="your-namespace"
You can omit the --version parameter entirely to automatically pull the latest chart version. To install a specific version, use --version X.X.X (for example, --version 25.11). Note that Helm does not support --version latest syntax.
Replace the following placeholders with your actual credentials:
default: Replace with the Kubernetes namespace where you want to install Invicti NTA. This should also be the namespace watched by Envoy.email-address: Replace with your Invicti Platform email address.password: Replace with your valid Invicti Platform license key.registration-token: The registration token from Step 1.8. Keep it enclosed in double quotes.your-namespace: The target namespace (should be separate from your application namespace). This namespace does not requireistio-injection=enabled.
Run the command to install Invicti NTA in your specified namespace and enable Envoy WASM filters to monitor traffic within that namespace.
Step 5: Verify the installation (optional)
To ensure that the installation was successful and the components are running properly:
- Run the following command to select the pod status:
kubectl get pods -n <your-namespace>
- Confirm that all pods (for example, tap, reconstructor) are not in CrashLoopBackOff or Error states.
- If any pods are not running properly, investigate their logs with:
kubectl logs <pod-name> -n <your-namespace>
Copy and paste the pod-name from the kubectl get pods -n <your-namespace> output.
If everything looks good, your Invicti NTA with Istio Service Mesh is now successfully capturing and analyzing traffic in your Kubernetes cluster.
Update or reinstall Invicti NTA with Istio
- Retrieve the latest registration token and password as outlined in the standard Invicti token generation procedure.
- Log in to the Invicti registry as in Step 2 preceding.
- Prepare and run the update command:
helm upgrade --install invicti-api-discovery \
oci://registry.invicti.com/invicti-api-discovery \
--version 25.11 \ # Optional: omit to pull the latest version
-n default \
--set trafficSource.envoyWasm.enabled=true \
--set imageRegistryUsername=email-address \
--set imageRegistryPassword=password \
--set reconstructor.JWT_TOKEN="registration-token" \
--set trafficSource.envoyWasm.namespaces="your-namespace"
You can omit the --version parameter entirely to automatically pull the latest chart version. To install a specific version, use --version X.X.X (for example, --version 25.11). Note that Helm does not support --version latest syntax.
Troubleshooting
For common issues including authorization failures, retry behavior, and resolution steps, refer to NTA troubleshooting.
Need help?
Invicti Support team is ready to provide you with technical help. Go to Help Center