Review scan results
The All scans page provides a list of all scans performed, including information about the scan profile, the time and date when the scan was performed, a count of vulnerabilities found for each severity level, and the current status of each scan. Findings that can be attributed to API specs are flagged with an API tag. API specs can come from manual uploads to a target/scan configuration, linked to a target/scan configuration, or linked from API Discovery.
From the All scans page, you can access the results of each scan, which are displayed on the Scan Details page. This document provides high-level information about the Scan Details page and the information you can review there.
Access scan results
When a scan is complete, Invicti emails you a summary of the results and a link to access the scan results directly. You can also access the scan results by following these steps in Invicti:
-
Select Scans > DAST scans from the left-side menu.
-
Click on the target for the relevant scan.
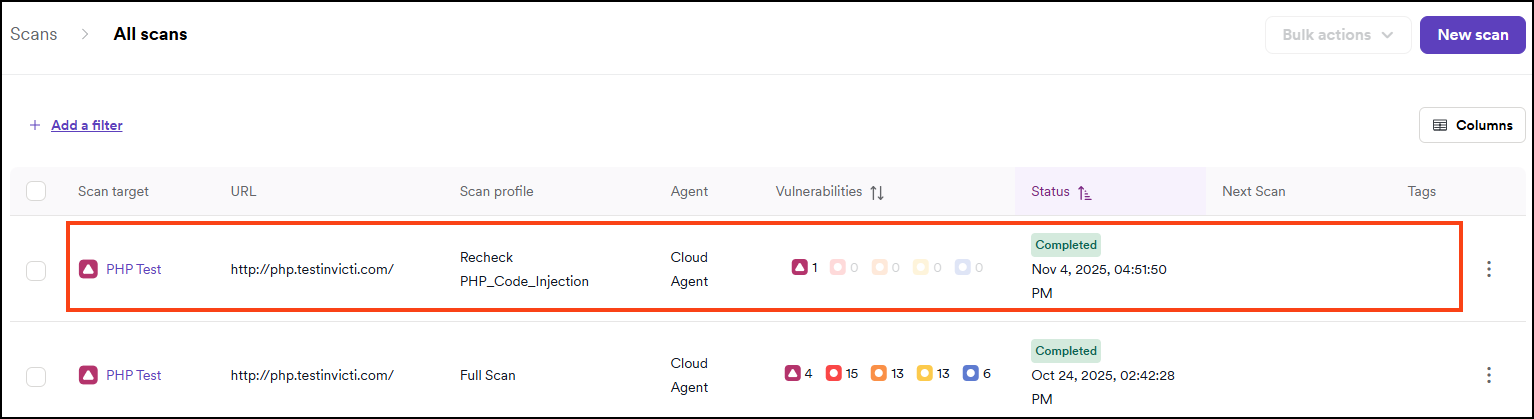
- The Scan details page opens. Use the tabs to view the scan results information.
For recurring scans, only the latest scan result for a specific target is displayed when you open the scan. In contrast, if you run multiple scans manually, each result is shown separately.
The Scan Details page provides information about the scan results, grouped under six tabs. Each tab is explained following.
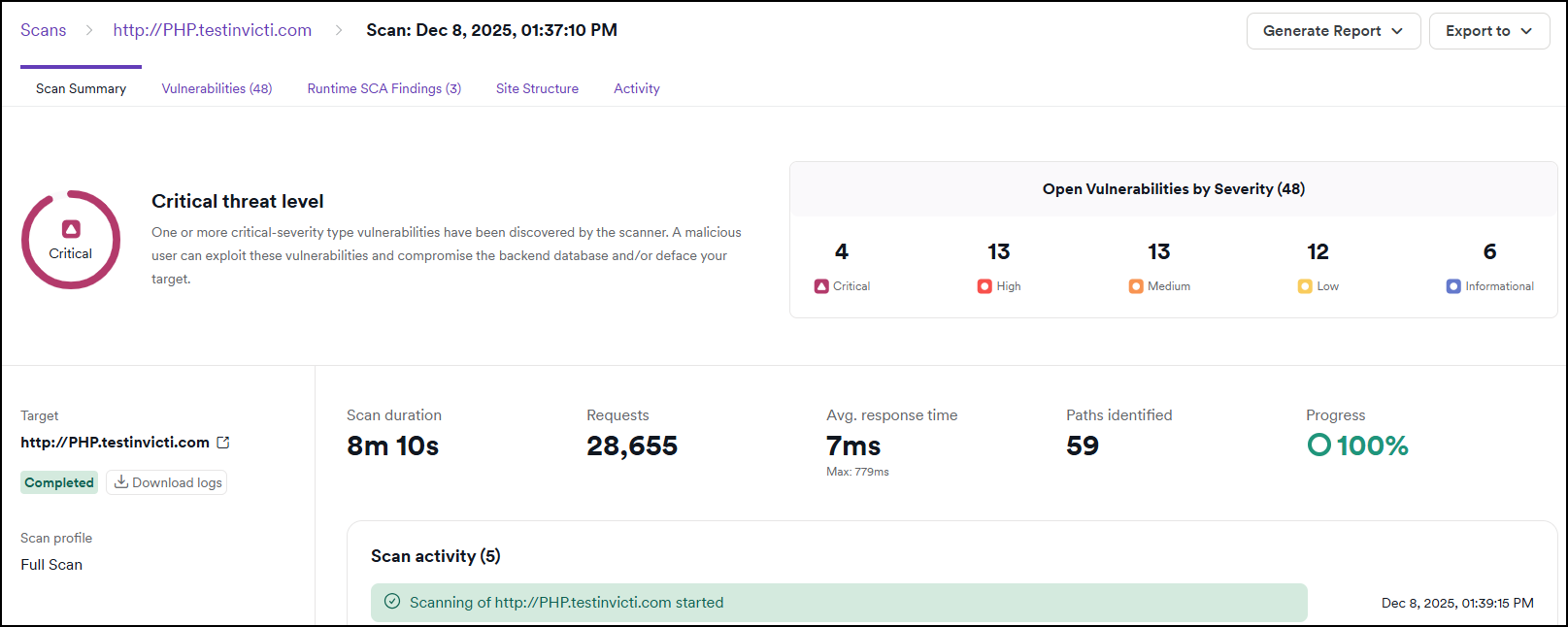
Scan summary
The Scan summary tab provides an overall threat level rating for the target based on the number and severity of vulnerabilities discovered by the scanner. It also displays the number of open vulnerabilities by severity, a summary of the scan parameters and activities during the scan, and the most vulnerable technologies detected on the target.
For detailed troubleshooting and analysis, you can download the complete scan logs from this tab, which provide comprehensive information about the scanning process, including HTTP requests, security checks, and performance metrics.
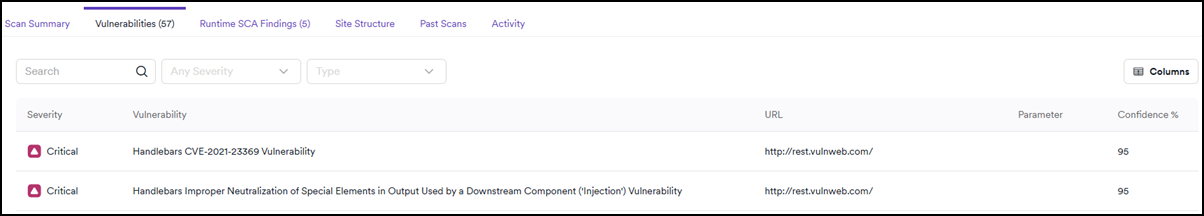
Vulnerabilities
This is the list of detected vulnerabilities, ordered by severity. You can filter the information by severity and target type. For example, you may choose to view only Critical and High severity vulnerabilities.
On the right-hand side, you have the option to change which columns are displayed. Click a vulnerability from the list to view all information about the detection and to change the vulnerability status.
If Invicti doesn't find a vulnerability with an Open status in 3 consecutive scans, the system automatically changes its status to Fixed. For more information, refer to the Retest vulnerabilities document.
To learn more about the vulnerabilities detail refer to the linked document.
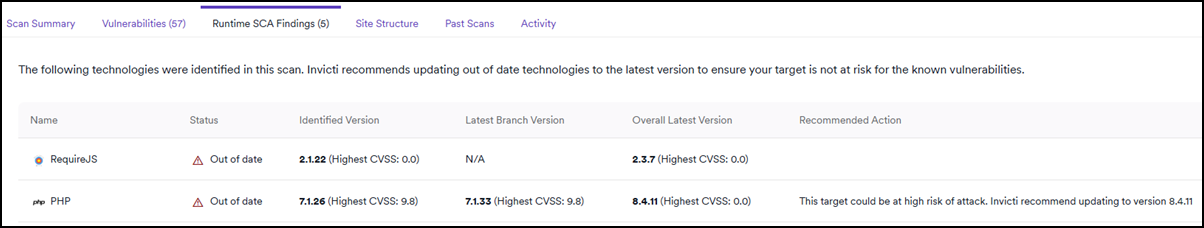
Runtime software composition analysis findings
This tab is only available for scans that were run using the Full Scan profile. Information isn't displayed if a different scan profile was used.
This section lists technologies used by the scanned target that have been identified as out of date. These aren't classified as active vulnerabilities and don't appear in the Vulnerabilities list. However, they may still pose a risk due to the use of outdated software versions.
Select Technology from the list to view details about its detection and recommended remediation steps.
For more information, see the documentation on Runtime SCA Findings.
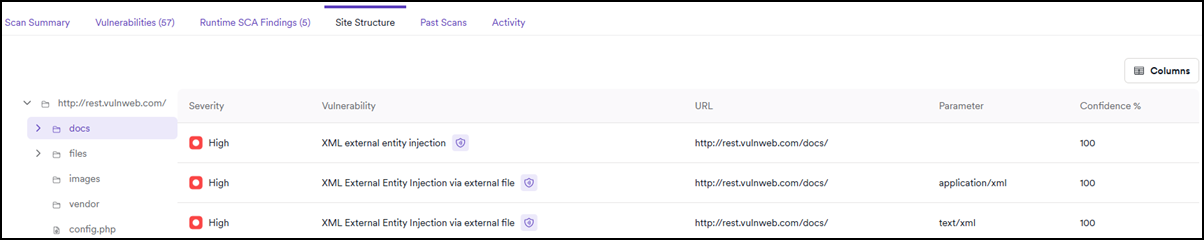
Site structure
Use this section to verify that the scan has covered all parts of your target and to identify vulnerabilities affecting a specific file or folder. Click Folder to expand the site structure tree and display the vulnerabilities detected in that part of your target. You can also click Vulnerability to show more information about the attack details, impact, and how to fix it.
Past scans
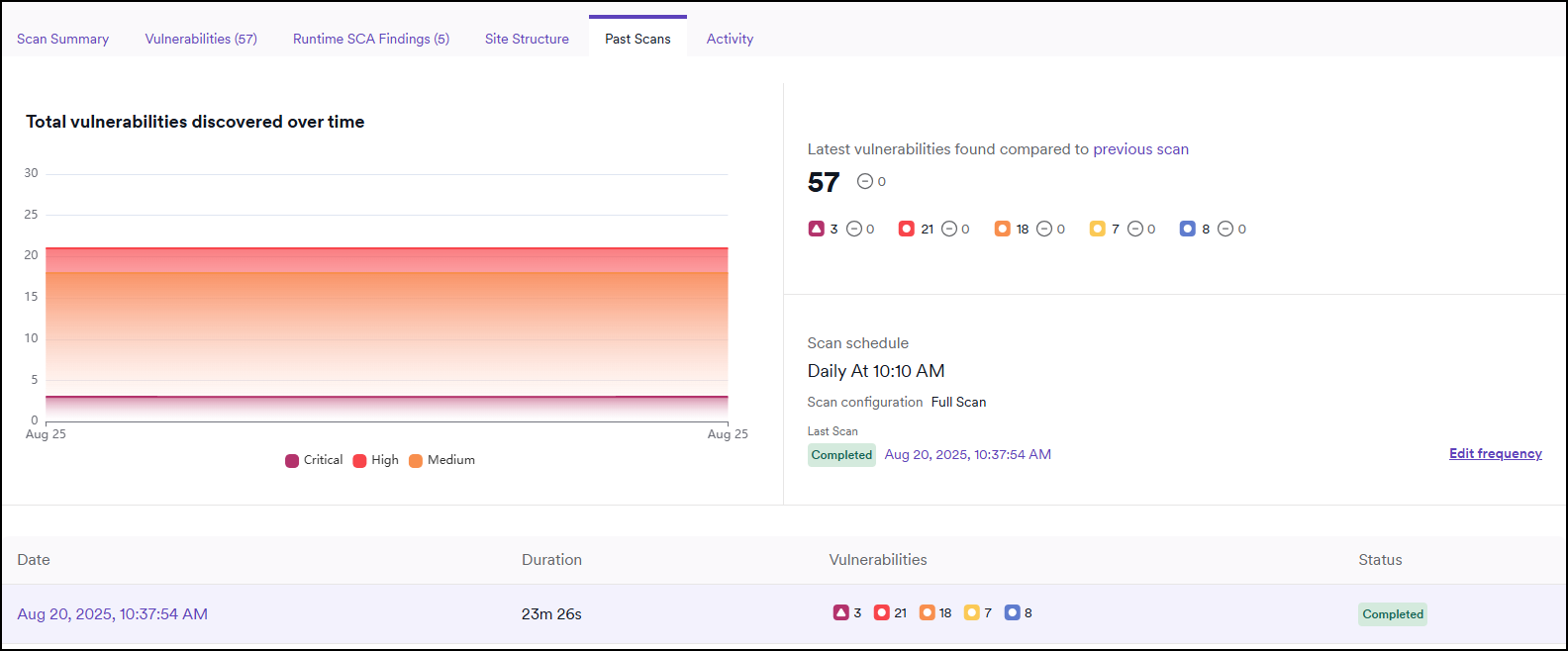
This tab is only available for recurring scans.
The Past scans tab allows you to access an overview and manage the scan schedule. You can see the summary of the last 10 scans, compare scans, and view the total number of critical, high, and medium vulnerabilities discovered.
Activity
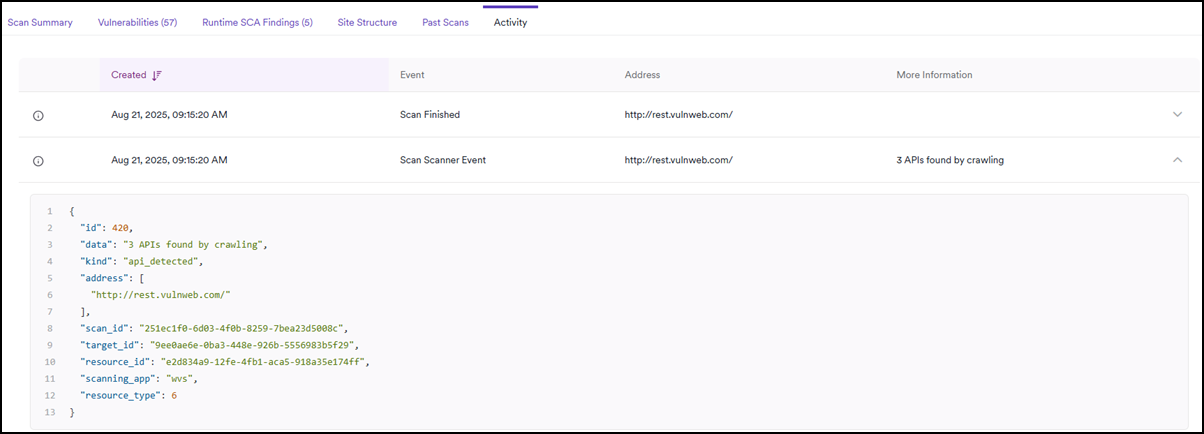
The Activity tab provides a list of the scan events, showing when the scan started and completed, and if any errors were encountered during the scan. Click on an item to reveal more details about the scan event.
Need help?
The Support team is ready to provide you with technical help. Go to Help Center