Okta Single Sign-On integration with SAML
Okta is an identity and access management platform. Its Single Sign-On (SSO) solution allows users to log into a variety of systems using one centralized process.
This document explains how to configure Okta and Invicti Platform for Single Sign-On.
Configure Okta with SAML
There are two steps in this process:
- Step 1: Add an application to Okta
- Step 2: Add users to the application in Okta
Step 1: Add an application to Okta
- Navigate to Okta's Admin Console, then select Applications > Applications from the left-side menu.
- Click Create App Integration.
- From the Create a new app integration dialog, select SAML 2.0. Then click Next.

- On the Create SAML Integration page, enter a name in the App name field. Invicti is used for this example.
- Select Next.
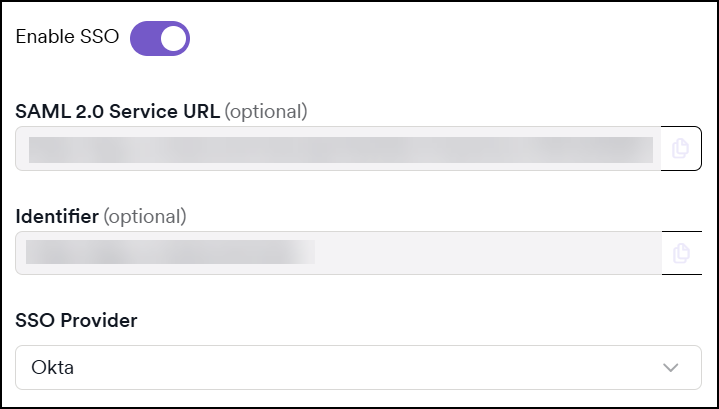
- In a new browser tab, login to Invicti Platform and select Settings > Security & access control > SSO & Provisioning.
- Turn on the Enable SSO toggle.
- Select Okta from the SSO Provider drop-down list.
- Copy the SAML 2.0 Service URL and paste the URL into Okta's Single Sign-on URL field.
- Return to the Invicti browser tab and copy the Identifier URL. Paste it into Okta's Audience URI (SP Entity ID) field.
- In the Okta tab, add the following FirstName field in the Attribute Statements and select user.firstName value from drop-down.

- Click Next to view the Feedback tab.
- Click Finish. The Invicti application's details appear.
- In the Sign On tab click View SAML setup instructions. Okta opens a new browser tab.
- From the new tab, copy the URL from the Identity Provider Issuer and paste the URL to Invicti's IdP Identifier field.
- In the Okta tab, copy the URL from the Identity Provider Single Sign-On URL and paste it to Invicti's SAML 2.0 Endpoint field.
- In the Okta tab, copy the content from the X.509 Certificate field. Then switch to the Invicti tab and paste the URL to the X.509 Certificate field.

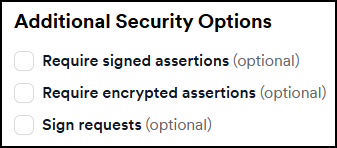
- In Invicti, select the checkboxes for signed assertions, encrypted assertions, or sign requests as needed.
warning
Selecting Require encrypted assertions requires applying additional settings in Okta. For instructions, refer to Configure encrypted assertions in Okta.
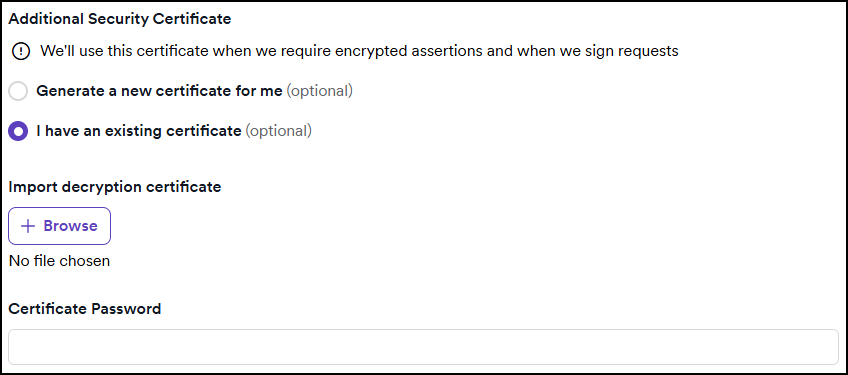
- If you enable any assertions or requests, a new section appears where you can Generate a new certificate or upload an existing one.
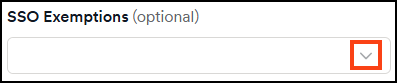
- Use the Invicti's SSO Exemptions drop-down to select users who can log in to Invicti via password.
- Click Save.
Configure encrypted assertions in Okta
- From Okta's main menu, go to Applications > Invicti.
- Select the General tab and scroll to the SAML Settings section. Click Edit.
- Click Next, then Show Advanced Settings.
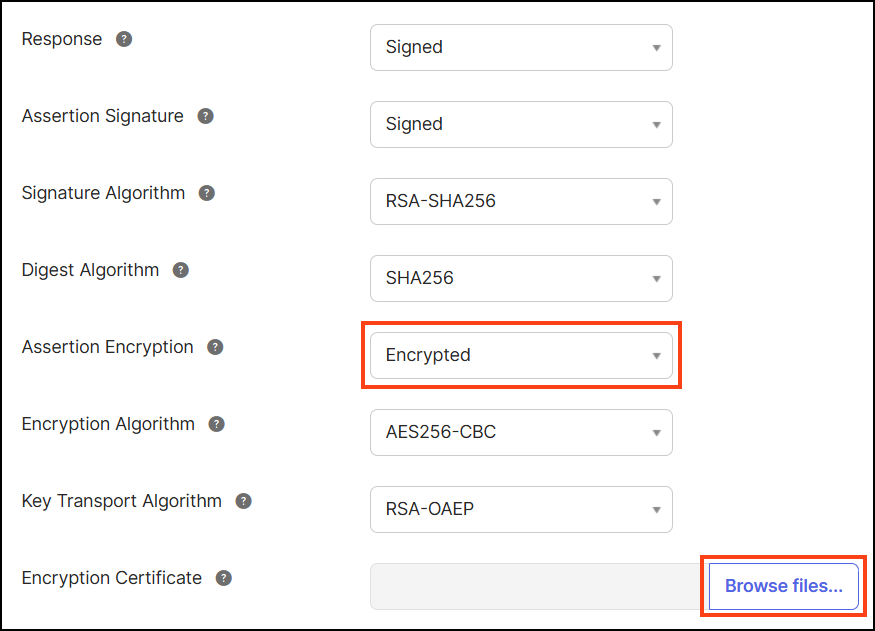
- Use the drop-down next to Assertion Encryption to select Encrypted.
- Click Browse Files next to Encryption Certificate and upload your Invicti certificate.
Step 2: Add users to the application in Okta
- Select Directory > People from the left-side menu in Okta.
- Click the Add Person button to open a form.
- Fill out the form.
- Click Save.
- Select Applications > Applications from the left-side menu.
- Select Invicti from the list.
- In the Assignments tab, click Assign > Assign to People.
- From the Assign Invicti to People dialog, select Assign next to the person you want to add.
- Select Save and Go Back.
- Click Done.
Your assigned users can now log in to Invicti via Okta.
info
To learn more about the Single Sign-On fields, refer to the Single Sign-On configuration document.
Need help?
Invicti Support team is ready to provide you with technical help. Go to Help Center
Was this page useful?