Report templates
In Invicti, you can generate and download a series of various types of individual scan reports, including compliance reports from a series of Report Templates.
In Invicti Enterprise and Invicti Standard, scan reports are accessed differently:
- In Invicti Enterprise, scan reports are accessed from the Recent Scans window.
- In Invicti Standard, scan reports are generated from the Reporting tab, along with Lists.
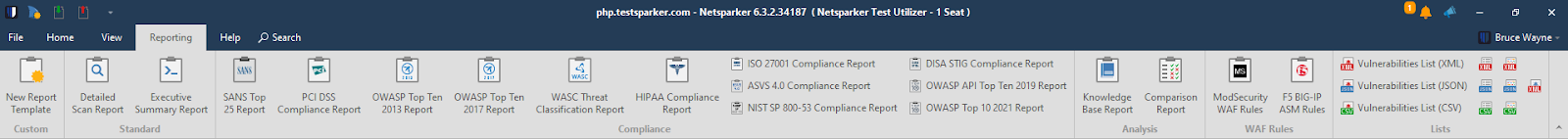
This table lists and explains the Report Templates.
| Report Template | Description |
|---|---|
| New Report Template | This is an Invicti Standard only feature that enables you to customize and name your own report template, using one of the other report templates as a Base Template. For more information on how to create your own custom report templates using the Custom Reporting API, refer to the Custom Reports document. |
| Detailed Scan Report | This is a detailed report that outlines scan details such as request, response, and vulnerability descriptions, including information on the impact of the vulnerability, remedy procedure, classifications, and proof URLs. This report also includes a summary of which settings were used. For more information, refer to the Detailed Scan Report document. |
| Executive Summary Report | This is a brief report that includes recommendations and summaries based on the most recent scan of the website. For more information, refer to the Executive Summary Report document. |
| HIPAA Compliance Report | This is a report that lists the vulnerabilities included in HIPAA standards along with their details. For more information, refer to the HIPAA Compliance Report document. |
| ISO 27001 Compliance Report | This is a report that outlines the vulnerabilities included in the ISO 27001 standard along with their details. For more information, refer to the ISO 27001 Compliance Report document. |
| DISA STIG Compliance Report | This is a report that outlines the vulnerabilities included in the DISA STIG standard along with their details. For more information, refer to the DISA STIG Compliance Report document. |
| NIST SP 800-53 Compliance Report | This is a report that outlines the vulnerabilities included in the NIST SP 800-53 standard along with their details. For more information, refer to the NIST SP 800-53 document. |
| OWASP Top Ten 2013 Report | This is a detailed report that outlines the OWASP Top Ten 2013 vulnerabilities along with their details. For more information, refer to the OWASP Top Ten 2013 Report document. |
| OWASP Top Ten 2017 Report | This is a detailed report that outlines the OWASP Top Ten 2017 vulnerabilities along with their details. For more information, refer to the OWASP Top Ten 2017 Report document. |
| OWASP Top Ten 2021 Report | This is a detailed report that outlines the OWASP Top Ten 2021 vulnerabilities along with their details. For more information, refer to the OWASP Top Ten 2021 Report document. |
| ASVS 4.0 Compliance Report | This is a detailed report that outlines the OWASP ASVS 4.0 vulnerabilities along with their details. For more information, refer to the ASVS 4.0 Compliance Report document. |
| OWASP API Top Ten 2019 Report | This is a detailed report that outlines the OWASP API Top Ten 2019 vulnerabilities along with their details. For more information, refer to the OWASP API Top Ten 2019 Report document. |
| PCI DSS Compliance Report | This is a report that lists the vulnerabilities that are listed in the PCI classification along with their details. For more information, refer to the PCI DSS Compliance Report document. |
| SANS Top 25 Report | This is a report that outlines the CWE/SANS Top 25 vulnerabilities along with their details. For more information, refer to the SANS Top 25 Report document. |
| WASC Threat Classification Report | This is a report that lists the vulnerabilities in the WASC threat classification along with their details. For more information, refer to the WASC Threat Classification Report document. |
| Comparison Report | This is a detailed, Invicti Standard only, report that includes compared results between more than one scan. For more information, refer to the Comparison Report document. |
| Knowledge Base Report | This is a report that lists the Knowledge Base details of the scan. For more information, refer to the Knowledge Base Report document. |
| F5 BIG-IP ASM WAF Rules | This is a report that lists the vulnerabilities according to the BIG-IP ASM WAF Rules. For more information, refer to the F5 BIG-IP ASM WAF Rules Report document. |
| ModSecurity WAF Rules | This is a report that lists the vulnerabilities according to the ModSecurity WAF Rules. For more information, refer to the ModSecurity WAF Rules Report document. |
For more information on how to modify the way vulnerabilities are reported during a scan, and report them to match your organization's security policies, refer to the Custom Report Policies document.
For more information on how to generate and download Vulnerabilities Lists, as well as Scanned URLs and Crawled URLs lists in both Invicti Enterprise and Invicti Standard, refer to the Lists document.
Use your company logo in a report in Invicti Standard
This replaces the Invicti logo in the report.
- Navigate to
C:\Program Files (x86)\Invicti\Resources\Images\. - Save your preferred logo as
logo.gifin the Images folder. - You can now generate reports with your company's logo, without needing to restart Invicti.
Need help?
Invicti Support team is ready to provide you with technical help. Go to Help Center